The 2022 Credentials and Credential Management BIG DEAL!
A reliable, easy-to-adopt and comprehensive credential solution is in this article.

Are you tired of keeping track of the smartphones, tablets and workstations used at your company’s offices, and need a solution that supports not only Active Directory but macOS-based workstations?
So, whether you are in the business world in sectors such as infrastructure, healthcare or finance or are in state and local governments, WorkforceID Digital Credential Management has you covered.
Do you want an all-in-one software suite that actually allows for users to manage their own devices to take more of the workload off your plate?
Well, HID WorkforceID Digital Credential Management is the next step for your business to manage all of the credentials that your employees have and use on a daily basis. With the many devices that we all use day-to-day, you need a solution that is both reliable and easy-to-use for your users, that is where Digital Credential Management comes in.
With a cloud-based foundation and a subscription-based model, you will not think about any sort of troubleshooting.
There are many more features that you can find out about down below!
But, before we start talking about the features, let us speak about who HID Global and Tx Systems are.

REACH OUT today about the WorkforceID Digital Credential Management offer today by calling us at 858-622-2004 or sales@txsystems.com.
Who is HID Global?
This Irvine, California-based cybersecurity company founded in 1991 as Hughes Identification Devices has technology solutions used in more than 100 countries over 2 billion trackable objects. It is a 650 employee manned-subsidiary of ASS ABLOY AB which has a over $3.2 billion of revenue in the locking solutions sector.
It is a trusted leader in the delivery of secure identity and logical access cards (iCLASS, SEOS) and hardware (OMNIKEY product line). These are reliable solutions that provide businesses with the protection that they need to lock down their physical and digital assets, so they can continue to provide their customers with exceptional service.

Who is Tx Systems?
Tx Systems knows a thing or two about credential management and identity solutions as we have been in the business since 1997 and have worked with some of the largest players (Fortune 500) in multiple verticals. We are the ideal reseller of major smart cards types conforming to ISO 7816 (Smart Card Industry Standard) and smart card readers, from trusted and respected manufacturers such as HID which we are an official Platinum Partner. We also offer many MFA (multi-factor authentication) solutions from HID such as WorkforceID Digital Credential Management along with DigitalPersona which we support with our one-on-one technical support, so you will not be left in the dark.
With Tx Systems, you can rest assured that your data is secure for your business and its unique needs.

Features:
- Provides Secure Access: to your business’ VPN (Virtual Private Network), cloud and web applications such as productivity software and Windows-based shared workstations through Azure Active Directory (AD) and physical access control to your office building
- SUPPORTS BOTH PHYSICAL AND LOGICAL ACCESS to save money from needing to invest in multiple solutions for both applications

- FLEXIBLE use cases for WorkforceID such as secure printing, email and file encryption and digital document signature to ensure further security for entire organization
- Compliant with Major Industry Standards/Regulations: NIST, FIPS, GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), HIPPA (Health Insurance Portability and Accountability Act) PSD2, PCI-DSS, GLBA, SOX, SP800-171 (Controlled Unclassified Information), CJIS, NY DFS 23, NYCRR, IRS pub 1075 (IS Guidelines for Federal, State and Local Governments) and NERC-CIP
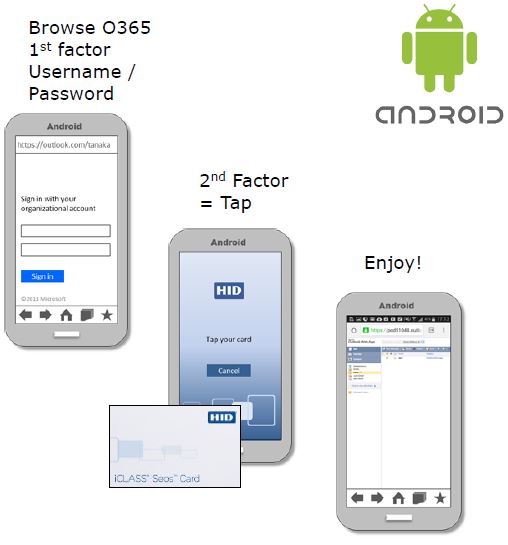
- Strong Security and User-Friendly: PKI (Public Key Infrastructure) certificate management on Crescendo 2300 Smart Cards, Crescendo 144K FIPS or other offered third-party solutions which allows for both PKI (Public Key Infrastructure) and OTP (One-time Password) credential management to be much more streamlined
- PIV-compatible: Integrates with Windows Active Directory (AD) and Azure Active Directory (AD) on Windows 10 and 11 (64-bit edition) workstations but also works well with macOS 10.15 (Catalina) and 10.16 (Big Sur) workstations for a wide support of major operating systems to be easily deployed in your office

- An Understandable Web Portal for Employees: Employees have the ability to reset PINS and manage their work devices such as security keys, OTP (One-Time Password) tokens and more while adding additional credential hardware devices when needed
- Report lost devices and easily issue new devices to replace the old device
- Credentials are managed for the entire time that the employee is employed and can be deleted once they leave
- Ease of Deployment and Maintenance: All-in-one cloud-based web portal that creates, manages and uses credentials for both hardware and software saving maintenance time as you have the latest updates and patches
- Saves Money: Supplemental material and software licenses are not costly given the cloud-based subscription format
- Easy Renewal: Subscription license per user per year
- Choice of Trust Model: HID WorkforceID Digital Credential Management takes care of the certificate authority portion of management which can either be Publicly or Privately managed which are of no additional cost for PKI (Public Key Infrastructure)
- Allows you to use MFA (multi-factor authentication) without hassle

- Reliable: HID’s WorkforceID webportal uptimes are 99% available for both the management of the Digital Credential Management portal as well as for using the portal for PKI (Public Key Infrastructure) validation allowing for seamless workflow
- 24×7 Customer Support: You have the technical support that you need wherever you are in the world.
- Leave a Paper Trail: Status and audit reports are available for download to meet compliance requirements and reduce liability costs.
Where Can I Find Out More About WorkforceID Digital Credential Management?
Breathe a sigh of relief knowing that you have solved your credential hassles at work! You have achieved the goal that you set out today at work and have found a solution to make your boss happy.
Take advantage of our latest deal with HID Global where you can save on a year-free of HID WorkforceID Digital Credential Manager when you purchase an order of 100 HID Crescendo Security Keys or HID Crescendo 2300 Smart Cards. Utilize both of these technologies to not only login to your workstation but also access your business’ locations.
REACH OUT today about the WorkforceID Digital Credential Management offer today by calling us at 858-622-2004 or sales@txsystems.com.

Author: Carl Hughes, Sales/Marketing Specialist
A technical hobbyist interested in learning the nitty-gritty of computers.